This blog was prompted by the AWS announcement in July 2023 that with effect from February 1, 2024 there will be a charge for all public IPv4 addresses, whether or not it is attached to an EC2 instance:
https://aws.amazon.com/blogs/aws/new-aws-public-ipv4-address-charge-public-ip-insights/
For some customers, this could become a significant cost. The following AWS blog does give some insight into how to reduce costs, by using Elastic Load Balancing or NET Gateways to reduce your usage of IPv4 address space:
In practice, there will be many cases where you will have to continue to use IPv4. There may be clients which want to access your AWS services, but do not support IPv6. One example I came across is a home router used by a well-known home broadband provider. Whilst my laptop and browser support IPv6, I cannot run it from home because this router does not currently allow it. Home ISPs, please note!
Also, some AWS services do not support IPv6 yet. See the following URL for the full list:
https://docs.aws.amazon.com/vpc/latest/userguide/aws-ipv6-support.html
So, in practice, we may have no choice but to implement a so-called "dual stack" approach, at least in the short term.
However, if we disregard these issues, is it possible to create a single IPv6-only environment? To answer that, we first need to understand some of the key differences between IPv4 and IPv6.
IPv6 compared with IPv4
Aside from the different numbering terminology (IPv4 uses a dotted decimal 32-bit notation, whereas IPv6 uses hex notation for a 128-bit number), one key difference between the different systems is the use of public-facing and private addressing.
In IPv4, there are certain address ranges defined by RFC 1918 which the Internet Assigned Numbers Authority (IANA) has reserved for private networks:
- 10.0.0.0 - 10.255.255.255 (10.0.0.0/8)
- 172.16.0.0 - 172.31.255.255 (172.16.0.0/12)
- 192.168.0.0 - 192.168.255.255 (192.168.0.0/16)
Is an IPv6-only EC2 Stack possible?
Suppose you have an EC2 instance hosting a web server is using an IPv4 Public IP address. If you browse to your website (e.g. http://ec2instance.amazonaws.com ), the DNS service will resolve that domain name into a public IPv4 address such as 78.65.4.80. Subsequently, the IPv4 protocol will send packets to that address.
With IPv6, on the other hand, we want the domain name to be resolved into an IPv6 address such as 2001:::c4:e6:86. Assuming that our browser supports IPv6 (most modern ones will do), then it will send packets via IPv6 to that address.
In order to implement this, we need to make some changes to our underlying VPC and subnets, and to the launching of the EC2 instances themselves.
VPC Configuration changes
We then need a suitable IPv6 address range. However, unlike IPv4, we cannot easily specify this ourselves. Instead, AWS provides one fixed size (/56) IPv6 CIDR block. Large enterprises may want to control their own IPv6 address allocation. This can be done by using "bring your own IPv6" (BYOIPv6). But for the purpose of this blog, we can accept the address allocation from Amazon.
The following graphic shows the AWS console page for provisioning the VPC:
- Provision the VPC as a Dual Stack with both IPv4 private address range, and an IPv6 address range
- Provision an Internet Gateway and attach it to the VPC, as before.
Public Subnet changes
The key changes we need to make in a Public Subnet are:
- Provision the subnet to be IPv6 only.
- Disable the auto-assign public IP address option.
- Ensure that DNS hostnames and DNS resolution are both enabled.
- Add an IPv6 default address route (i.e. :/0) to the Internet Gateway. But we do not need a default address route for IPv4.
- Ensure that the security group allows incoming traffic from the internet (:/0) on IPv6, and that the Network ACL (NACL) also allows the traffic using IPv6
Private Subnet and Firewall changes
- Provision the subnet to be IPv6 only.
- Provision an egress only internet gateway within the VPC.
- Add an IPv6 default address route (i.e. :/0) to the egress only internet gateway. This will expose the IPv6 address to the internet for Outgoing requests, but block requests coming from outside. We do not need a default address route for IPv4.
EC2 configurations
Amazon EC2 supports launching instances into IPv6-only subnets provided that they are based on the Nitro System.
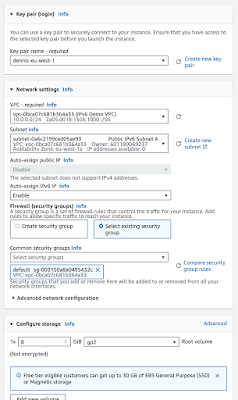
If we provision our EC2 instance inside a Public subnet, it will receive just an IPv6 address only. The following extract from the AWS console shows the "Auto-assign public IP" (meaning version 4) disabled, and the "Auto-assign IPv6 IP" enabled.
Once the EC2 instance has been launched, you can "ping" its IPv6 address, using the "ping6" command, or use an online site such as https://subnetonline.com/pages/ipv6-network-tools/online-ipv6-ping.php (don't forget to enable ICMP for IPv6 in the Security Group). Here is an example of the output of "ping6":
- When you launch an instance with IPv4, the private IPv4 address of the instance is included in the hostname. When used as the Private DNS hostname, it will only return the private IPv4 address (A record).
- When you launch an instance with IPv6, the EC2 instance ID is included in the hostname of the instance. When used as the Private DNS hostname, it can return both the private IPv4 address (A record) and/or the IPv6 Global Unicast Address (AAAA record).
If you run "nslookup" you should see this domain name resolve to an IPv6 address. You should then be able to browse to this address. When using "nslookup", you can add the "-q=aaaa" option to ask nslookup to return the resolved IPv6 addresses from the "AAAA" record instead of the normal "A" record:
Other Factors to consider
In this blog, I have only addressed the challenge of EC2 instances. I have ignored services such as Elastic Load Balancers, NAT Gateway or AWS Global Accelerators. And I have ignored complications such as VPC peering, and communicating with pre-existing IPv4 services.
There are other reasons why you might need to provision IPv4. For example, you might want to use SSH or RDP to connect to the instance. For this use-case, you can use EC2 Instance Connect, which now has the ability to connect to your instances using private IPv4 addresses.
For more information on how to take advantage of IPv6, and thereby save yourself money in using AWS services, I have used the following AWS resources:
IPv6 is certainly the way to go with networking in future. Let's hope that AWS continue to bring more initiatives to make this technology easier to implement.